Screaming Frog Guide To Doing Almost Anything
For profitable scraping job, you ought to make use of in between 50 to a hundred and fifty proxies at the same time. We use a really comparable service in BibSonomy to help our users whereas posting a new reference. Nohodo gives a free account for Content Grabber customers (as much as 5000 requests month-to-month at no cost). Header values go unnoticed by the customers but can carry essential information such as the browser type. There could also be restrictions applied on what web sites you possibly can download knowledge from. Once you examine their IPs in IP checking websites you will see real residential ISPs, not hosting centers. Our IPs will log on and offline at random instances. That is the rationale it is crucial to make sure you’re finding a means to guarantee your IPs aren’t restricted before you get the opportunity to work. Web proxy is the easiest method to cover IP. Be sure they have scalable options that would — handle all that unstructured net information. You may have little functionality to manage them.
By setting the server to expire the document based mostly on its modification time, you’ll be able to mechanically have caches mark it as stale a set period of time after it is changed. However until robots have rights, it is easier for everybody if they swallowed their pride and pretended to be human. It «reads» every type of information on display screen (JS, HTML, Silverlight and extra), plus you’ll be able to practice the software program to emulate human actions of varied complexity. A: I can not assure that and I believe the reply needs to be the «No»! From this basic start line, further particulars will be added by scraping social exercise over lengthy periods of time and in search of actions which point out buying preferences, developments and interests. Which is your favourite net device or add-on? It is usually onerous to jot down these programs because it’s troublesome to determine the online requests essential to do the simulation. Scraper API supplies you unlimited bandwidth that gives a velocity of 100mbps that is perfect for web crawlers. 12000, their packages are mounted and provide limitless bandwidth.
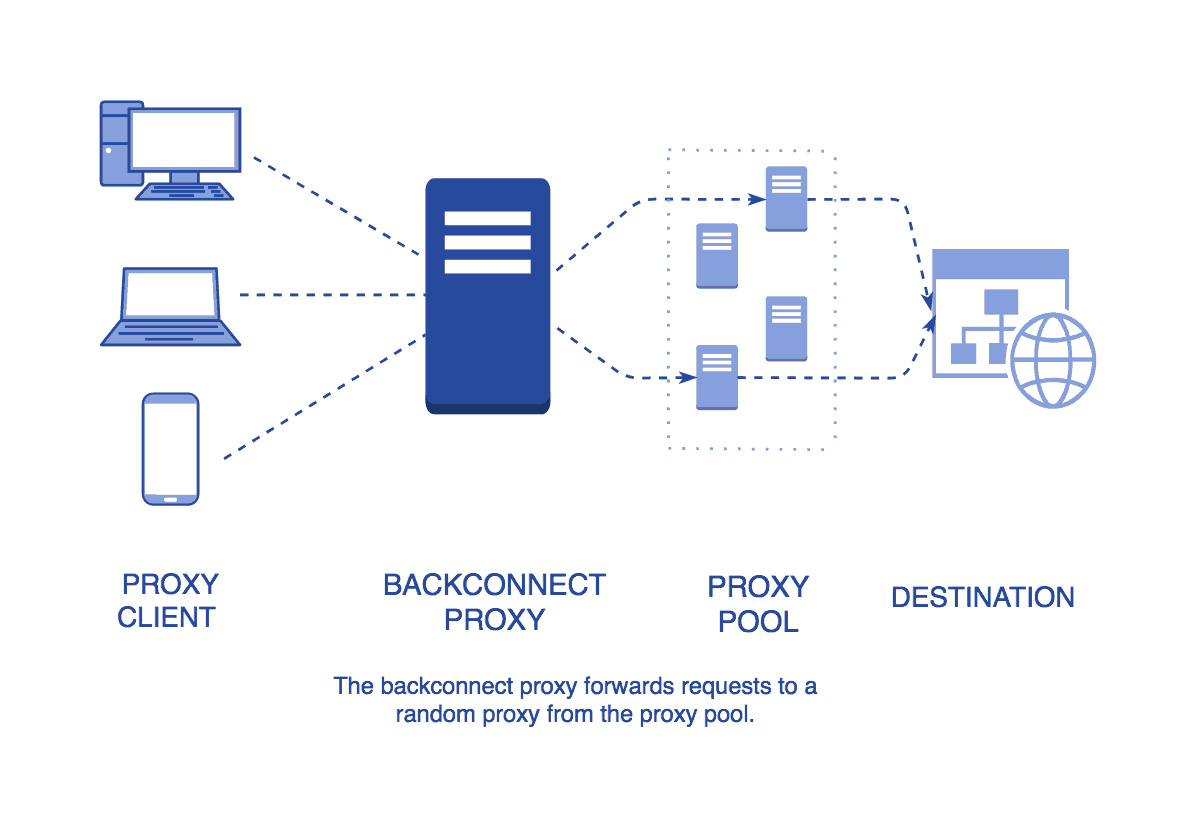
Using an this type of appliances minimizes the chance that any specific server shall be overwhelmed and optimizes the bandwidth available to each computer or terminal. It is possible to manually assign a performance weight to each server within the vacation spot group, and a scheduling sequence is automatically generated in line with the server weight. It would not be potential to build Apify without all the open-supply software on the market. I ‘m working in part of coding and software program growing for over 6 years. The servers of ProxyRack is having over 99.9% uptime and it can even hold a whole lot of concurrent connections. Simply put, you can observe this information and every little thing you have to know about it’s talked about in there. There isn’t any need to grasp the code and writing scripts on webpages. There are two essential disadvantages to utilizing a backconnect proxy, and the primary one is the cost.
When you find yourself browsing with a proxy, your Web site visitors is routed through that server, making it look as if it came from the server’s IP handle Purchase Shared Proxies. In case you look at the modem and the lights are green, it’s not likely to be a line difficulty. It’s as simple as that. The Captcha will definitely develop a verification cookie that allows you to proceed. After about in the future the captcha web page is eliminated once more. Can I cost-effectively accumulate the information wanted to grow my business? HTML response knowledge will even be parsed automatically, by utilizing NekoHTML which corrects the XML stream before it’s handed to the XmlSlurper. If the community is using wireless encryption, though, you can be introduced with a display screen asking you to enter the wireless encryption password as shown beneath. The C&C server doesn’t upload further modules similar to VNC, password stealer, FtpGrabber.
Свежие комментарии